Watch out for this fake Android security update — it's really malware
Watch out for this fake Android security update — information technology's really malware

The notorious FluBot Android banking Trojan has a new, grimly amusing play tricks up its sleeve: It tries to fool you into downloading a imitation "security update" by warning you lot about ... FluBot itself.
"Your device is infected with the FluBot malware," reads a stark ruby screen that you lot'll see if you click on a link in a text message. "Android has detected that your device has been infected."
- Your Apple Pay money can exist stolen over the air — here's what to do
- The all-time Android antivirus apps
- Plus: Samsung Galaxy S22 vs. Phone 13: Can Samsung beat Apple?
In fact, your device has NOT been infected yet. But it will be if you practise what the message suggests: "Yous must install an Android security update to remove FluBot."
The actual alarm about this fake alert came last week from New Zealand's Figurer Emergency Response Team (CERT NZ), a government bureau that alerts citizens and enterprises about cybersecurity threats. (Many countries have a CERT; the U.S. somehow has two.)
If you are seeing this page, it does not mean yous are infected with Flubot however if yous follow the false instructions from this page, information technology Will infect your device. https://t.co/KrcPhCQB90September 30, 2021
When final we checked in on FluBot, it lured you in with a text bulletin telling you virtually a trouble with a package commitment. A link in the message you lot to a bogus page that said you had to download and fill up out a form to go your packet. You'd exist infected yous with FluBot if you followed the instructions.
Yous may still go that package-delivery detect, said CERT NZ, which led off with a tweet near the new variant and then followed up with a blog mail service. Or you might be texted a bogus warning that naughty photos of you had been put online.
Sometimes you'll get an epitome of a friendly young adult female holding a parcel with the traditional "awarding form" to download and fill out. Sometimes you lot'll get the scary image beneath. (We appreciate the humor of putting a registered-trademark symbol next to the proper noun of the malware.)
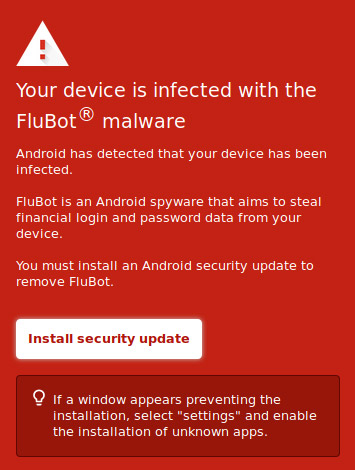
How to avert being infected past FluBot
"The malicious app will just infect your phone if [you] click the link AND download the app," CERT NZ's web log post said. "Receiving the text does not mean you are infected. Apple phones can receive the message but cannot be infected."
That's very truthful. And then are two statements in the bogus FluBot warning screen itself.
"FluBot is an Android spyware that aims to steal fiscal-login and countersign data from your device," it states. If you lot take problem installing the fake "Android security update," then you need to "select 'Settings' and enable the installation of unknown apps."
That'due south because by default, Google-provisioned Android phones will install apps simply from the official Google Play Store unless the user overrides those settings. That'south what the fake warning/real FluBot wants you lot to exercise. Don't do it.
Instead, make sure the default app-loading settings are on. In Android 8 or afterwards, go to Settings > Apps > Special access > Install unknown apps, and then make sure that "Non allowed" is next to each app name. If you encounter an "Immune", tap on the app and toggle off the switch.
In Android seven or before, go to Settings > Security (or Lockscreen and Security), where you lot'll meet an entry labeled "Unknown sources." Make certain it'due south toggled off.
You'll also want to be running one of the best Android antivirus apps. FluBot has been effectually for almost of 2021, so most antivirus apps will recognize and block it correct away.
FluBot outset appeared in Spain in early 2021, spread to other European countries and at present is expanding worldwide.
If y'all get an SMS text message that a package is waiting for you — or especially if y'all get a text that seems to be nearly an expensive detail, similar an iPhone thirteen, that's but waiting to be picked upward — be very very wary. Don't download random software from links that show upwards in text letters, and definitely don't enable unknown sources or unknown apps.
Source: https://www.tomsguide.com/news/flubot-warning-fake-security-update
Posted by: pinsonhalm1953.blogspot.com


0 Response to "Watch out for this fake Android security update — it's really malware"
Post a Comment